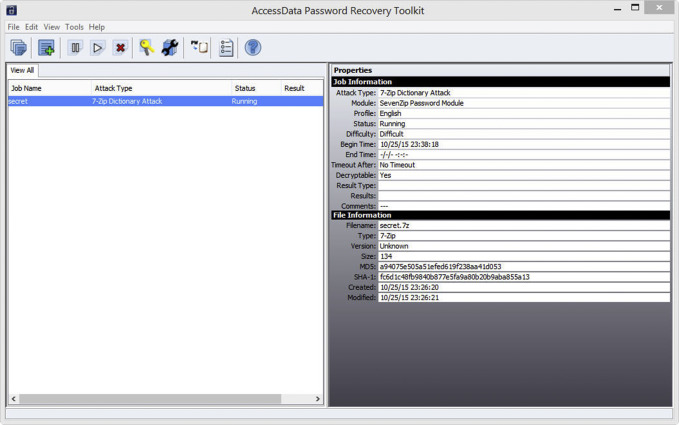
- How to crack Cisco Type 5 (MD5) Passwords By LineVTY Cisco 0 Comments Whilst Cisco’s type 7 passwords are incredibly easy to decrypt ( PacketLife Tools is my goto), Type 5 passwords are currently not reversible that does not however mean they are not susceptible to brute force attacks.
- Dec 08, 2017 username test password 4VnN2pEtX1eZQP5L encrypted privilege 15 I know this hash type is the Cisco ASA ( -m 1410 in the hashcat command). There is another type of password hashing used on an ASA, done by entering the following command.
- A minimum length of 8 to 12 characters long, with long passphrases being even better
- Password complexity that means it contains at least three different character sets (e.g., uppercase characters, lowercase characters, numbers, or symbols)
- Password rotation – Passwords must be changed every 90 days or less
- Use of account lockouts for bad passwords, with a limit of 5 or fewer bad attempts
- 69% share passwords with colleagues to access accounts
- 51% reuse passwords across their business and personal accounts
- 57% who have experienced a phishing attack have not changed their password behaviors
- 67% do not use any form of two-factor authentication in their personal life, and 55% do not use it at work
- 57% expressed a preference for a login method that does not involve the use of passwords
- Dictionary attacks: Dictionary attacks rely on software that automatically plugs common words into password fields.
- Cracking security questions: Many people use the names of spouses, kids, other relatives, or pets in security questions or as passwords themselves. These types of answers can be deduced with a little research, and can often be found on your social media profile.
- Guessing simple passwords: The most popular password is 123456. The next most popular password was 12345. Other common choices are 111111, princess, qwerty, and abc123.
- Reuse of passwords across multiple sites: When one data breach compromises passwords, that same login information can often be used to hack into users’ other accounts. Reusing passwords for email, banking, and social media accounts can lead to identity theft.
- Social engineering: Social engineering is the act of manipulating others into performing certain actions or divulging confidential information It can be employed to trick targets into disclosing passwords.
Top 15 Principles of Password Management
- Personal Password Managers: Which manage passwords for individual users/employees for access to various applications and services.
- Privileged Password Managers: These specialized enterprise solutions secure and manage privileged credentials from a centralized, enterprise-wide password safe. Privileged credentials are the organization’s most sensitive secrets, providing privileged access for user accounts, applications, and systems. These are generally paired with privileged session management and are a core component of an enterprise privilege management platform.
Final Thoughts on Improving Password Security
KB ID 0000940
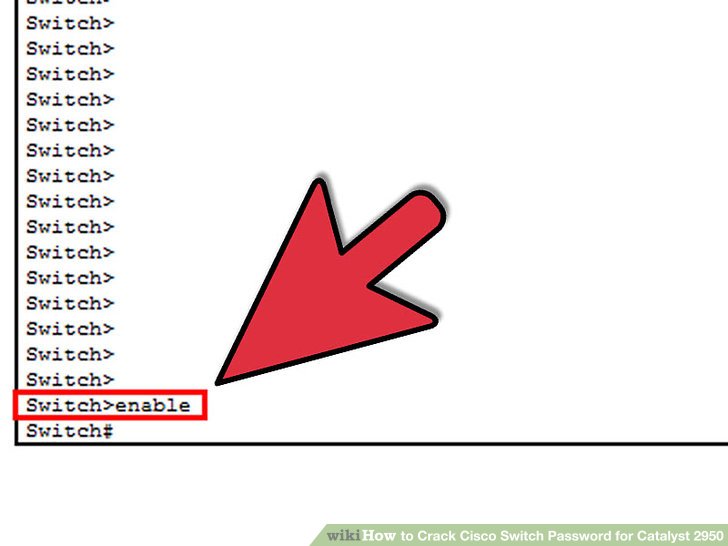
Problem
Decrypt Type 7 Cisco Passwords
The Internet is full of sites that have something like the tool below, tap your ‘encrypted’ password in and it will reveal the Cisco password.
As you can see I’ve specifically written ‘obfuscated’ above, because the password isn’t actually encrypted at all. All that happens is the Vigenere algorithm is used to obfuscate the password. While tools like the one above are all well and good, your Cisco router will do exactly the same for you, to demonstrate, paste the following into the tool above.
107D1C09560521580F16693F14082026351C1512
Hopefully you will get the password Sup3rS3cr#tP@ssword.
Your router can also convert that to clear text for you;
So whats the point of these type 7 passwords? Well the only real benefit of them is if someone is looking over your shoulder while you are looking at the config, they can’t see actual passwords in the config.
The passwords in my config are in clear text? That’s because there are three levels of password storage 0 (not encrypted), 7 (weakly encrypted), and (5 strongly encrypted). If you want to convert your config to display them as 7 you need to enter the service password-encryption command;
If Type 7 passwords are so weak, how do I use Type 5 passwords? When creating accounts use the secret command like so;
Displays in the config as;
